To secure your smartphone and tablet

To secure your smartphone and tablet
Not only on PC and notebook, more recently, the smartphone and tablet one is exposed vulnerabilities, malware and other attacks. Only those who protect themselves in time, can continue to surf safely through the Internet. We have tips on antivirus, anti-theft tools, and more.

We explain how their smartphone or tablet with anti-theft, anti-virus, and other security tools to secure or policies. Everyone is now more or less permanently online and utilizes both PC and notebook also powerful smartphones and tablets for a growing number of activities. The more important are mobile devices for us, the more interesting they are as targets for cybercriminals.
Equally important, each the safety of their own equipment should be, but according to the MSCI trial of Microsoft 77 percent of users do not worry – a dangerous recklessness , because pests such as viruses, Trojans and root kits provide next PC and notebook for mobile devices such as smartphones and tablets poses a growing risk dar. What you can do to protect yourself in advance, we will reveal the following.
Tip 1: Eyes on the app download:-

Before you download an app, you must first determine whether the source is trustworthy is. The official website of the developer is always worth a glance. This is linked directly to all app stores. If there is no reputable website with imprint, is care provided.
Helpful in this case is the predicate “Top Developer “, which is about Google awards in his Play Store for selected software vendor that not only deliver high quality, but also are very trustworthy. The quality seal can be found under the name of the developer on the app page.
Tip 2: Avoid unnecessary risks:-

It is also recommended that the installation outside of each official app stores to prevent default. This applies particularly to Android smartphones and tablets, as Google allows alternative sources. Such Android Apps APK file format can use their e-mail, obtained from the website of the developer or from an alternative app store.
To prevent such a malicious program is in this way able to unasked to install apps, you remove the “Settings / Security “to check” Unknown sources.” Of course, alternative app stores are not generally a threat or worse than the original, such as Amazon and Android PIT prove: So if you still want to install an APK file once, you can temporarily reactivate the above option.
Due to the closed app stores and a rigorous selection system that is part of Apple’s malware risk for iPhone and iPad owners been massively reduced. Watch should own a rooted, so unlocked iOS device: Get the app installation via appropriate IPA files is of course no problem.
It goes without saying that you pirated apps and software should avoid in any case. These are made ??available through illegal Internet sources, but are potential malware traps – read more on page 26 especially in the field of mobile apps, this tremendous risk not really worth now; especially when you consider that it usually is a saving of only a few Euros.
Tip 3: permissions as a gateway to the mobile device:-

Before you download the permissions that an app requests during installation. Depending on the program are Internet access and access to the internal memory normal permissions, without the many apps do not work. On the topic of location data should not be too sensitive – these are free apps for targeted placement of advertising.
But if an app wants to tap into for no apparent reason, the Google account, the contacts or the phone status, should the alarm bells ringing. Since consideration of the rights granted is difficult to judge, always read the comments of other users in the App Store to see the ordinary. Also install a security app (Tip 7), which warns you of dangerous apps. If in doubt, refrain from installing the app better.
Tip 4: No delay in updates:-
Even if you are in the installation of software and apps utmost care has done, there is the risk of programming errors and security vulnerabilities. Windows and Office Wore can keep up to date PC owners via the automatic update feature or by using our update package from the DVD booklet (see page 81).
Many programs that are not from Microsoft now have a function to update the lookout. To not have to do this manually for each tool, there is the “Sequoia Personal Software Inspector“(PSI), which can be found on the book DVD. To quickly find outdated versions and can be specifically get the updates.
Owners of smartphones and tablets should regularly bring their apps up to date. Call up the respective app store app under “My Apps” on. Using the “Refresh All “can then update all affected apps with a tap. This should make it possible in Wi-Fi to conserve the mobile data volume.
Once you have your apps in the handle, but you are already protected from the worst of danger for your smartphone or tablet. Nevertheless remain some important preparations so that you are protected in any situation: official updates for your operating system here are top on the list. Unfortunately not all companies automatically patches, so you may need to check on the official website of your device manufacturer.
Tip 5: Protection against Thieves:-

The easiest way to protect your data from prying eyes and thieves by the lockscreen of the smartphone or tablet with a password protects. The assurance by drawing a gesture or no backup is far more popular. By smudges on the screen, the gesture can not but rarely understand.
In the event that your phone is lost, there are anti-theft apps for your phone. The app from antivirus vendor Lookout, for example, is aiming to your device using Google Maps, you can send an alarm or make a picture of the person using the device. Even a remote encryption or even a system reset remotely possible – but only for the premium version of the app.
Even Windows users can protect their devices. This should be one for each user, password create. Do you have to leave work in the short term, it is enough to lock Windows using the keyboard shortcut “Windows + L”. However, Windows passwords are just a protective soft to discourage the curious.
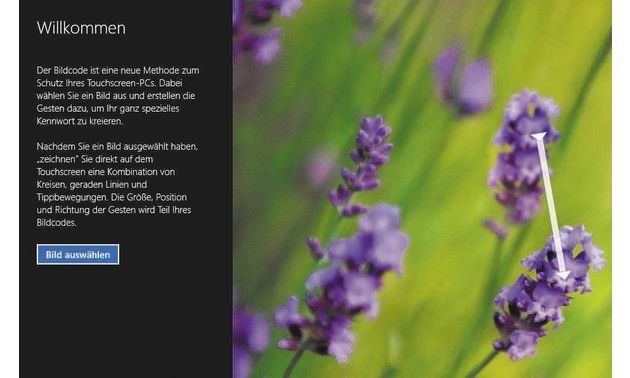
With tools such as the “Offline NT Password & Registry Editor “can be with little effort the Windows password easy to remove . Who has a Windows 8 has touch-screen device, should better protect this with a “gesture login.”
By taping the start screen right on top of his Avatar and select “Edit Profile Picture.” Then you tap the left to “User” and “create image code” in the right half of the screen on. Now you can from an input of lines and circles create a very individual login gesture.
Against thieves who want to steal all the same notebook, helps a ” Kensington Lock “.Some notebooks have this Anti-theft: This can be a cable with a special Kensington lock (from 10 Euros) engage in a slot on the notebook. The steel cable itself to tie it around a stationary object. Whose notebook does not have this protection, may resort to alternative safeguards, such as the PNY Think Safe (about 20 euros). Here the steel cable is attached via a locking hinge on the notebook.
Tip 6: Encrypt Sensitive Data:-
Save as little personal information as possible on your device: passwords or credit card details have lost nothing in the device memory. If you rely on to have access to critical data, To access all browsers offer the option to cache web services, but this is a risk.
Better to use a password manager service like Last Pass. This is available for both Windows and mobile devices. The password manager collects all your data and stores it encrypted. From now on, you have to sign only with a password and then are logged immediately in all your services.
Who stores its passwords locally rather, the tool should KeePass use. The thus generated password database can also be opened on mobile devices: With Astor File Manager (Android), Mini KeePass (iPhone) and 7Pass (Windows Phone 7/8) are appropriate mobile apps ready.
Sensitive documents should be stored in encrypted form on the notebook. This works very simply with True Crypt . The free tool creates container files that can be mounted as virtual drives in Windows Explorer. Is the notebook lost, the encrypted data is stored at least protected against abuse.
Tip 7: Always wear protective:-
“Install security software “- this truism may already be familiar with PC owners, but the reality is different. After the already mentioned at the beginning Microsoft study only 56 percent of PC users have installed an anti-virus software, 44 percent surf consequently exposed through the Internet.
It can be this recklessness easily prevent: Good anti-virus software you get even free, such as ” AVG Antivirus Free 2013 “. On mobile devices, the ratio looks even worse, but even here there is very good protection for free, such as “Lookout Security & Antivirus” for Android, iOS and Kindle. Even a locating device comes with the Lookout app to track missing devices again.

Best Apps to Have on your Phone - Both iOS and Android

Real Estate Social Media Post Design

Incoming Harvard College Students Admissions Essay Goes Viral On Tiktok

Essay Writing Service You Presumably Can Trust

Expert Installation: Tips for Choosing Air Conditioning in Brisbane

How to Maintain a Rotary Vane Air Compressor

Pet Hospital Logo Design Samples

